[ad_1]
Why it matters: Apple has been extolling the security architecture of iOS for years, but the locked-down nature makes it hard for security researchers to inspect the operating system and detect signs of a cyberattack. That’s why even a respected security firm like Kaspersky can spend years in the dark about a spyware campaign targeting its corporate devices.
Russian cybersecurity firm Kaspersky says it has discovered an “extremely complex” attack that affects all iPhones running iOS 15.7 or older versions but seems to be primarily aimed at iOS devices owned by Kaspersky management and key employees.
The timing of the report coincides with public allegations thrown by Russian intelligence at its US counterpart. The Kremlin’s Federal Security Service (FSB) claims that Apple has been working closely with the National Security Agency (NSA), providing the latter organization with a backdoor so that it could plant spyware on thousands of iPhones belonging to diplomats of Russia, NATO members, Israel, China, and some ex-Soviet nations.

Kaspersky is aware of the FSB claims but has been unable to verify if there’s a link between the two attacks. The company explains that while the spyware described by the FSB appears to be similar to the one it found on phones belonging to its top and middle-management, the Russian agency has yet to provide a technical analysis of the malware in question.
As for Apple, the company refused to comment on the accusations but wanted to note that “we have never worked with any government to insert a backdoor into any Apple product and never will.”
Circling back to the strain of spyware spotted by Kaspersky, it looks like yet another example of a zero-click attack. The researchers dubbed it Triangulation to highlight that it’s part of a stealthy intrusion campaign that uses Canvas fingerprinting to leave a yellow triangle in the target devices’ memory. After analyzing its own corporate network traffic, the company found the campaign is still ongoing and may have been active since 2019.
The attack chain starts with attackers sending victims a specially-crafted message via Apple’s iMessage service. Once received, a malicious attachment in the message automatically begins the exploit without the person in question opening the message or the attachment. Before the victim has a chance to delete the message, the malicious code executed through the exploit will have already downloaded the spyware that gives hackers deeper access to the target device.
Kaspersky researchers were able to analyze the infected devices by recovering data from backups made using the Mobile Verification Toolkit. They also note the malware they discovered will not persist on the device after a reboot, though they have seen evidence of reinfection for some of the affected phones.
As of writing, it’s unclear what vulnerabilities are used in the attack chain. However, Kaspersky believes one of the flaws is a kernel extension flaw tracked under CVE-2022-46690 that Apple patched in December 2022 with the release of iOS/iPadOS 16.2. At the time, the Cupertino company also started distributing iOS 15.7.2 to older devices with fixes for several high-risk, “actively-exploited” vulnerabilities.
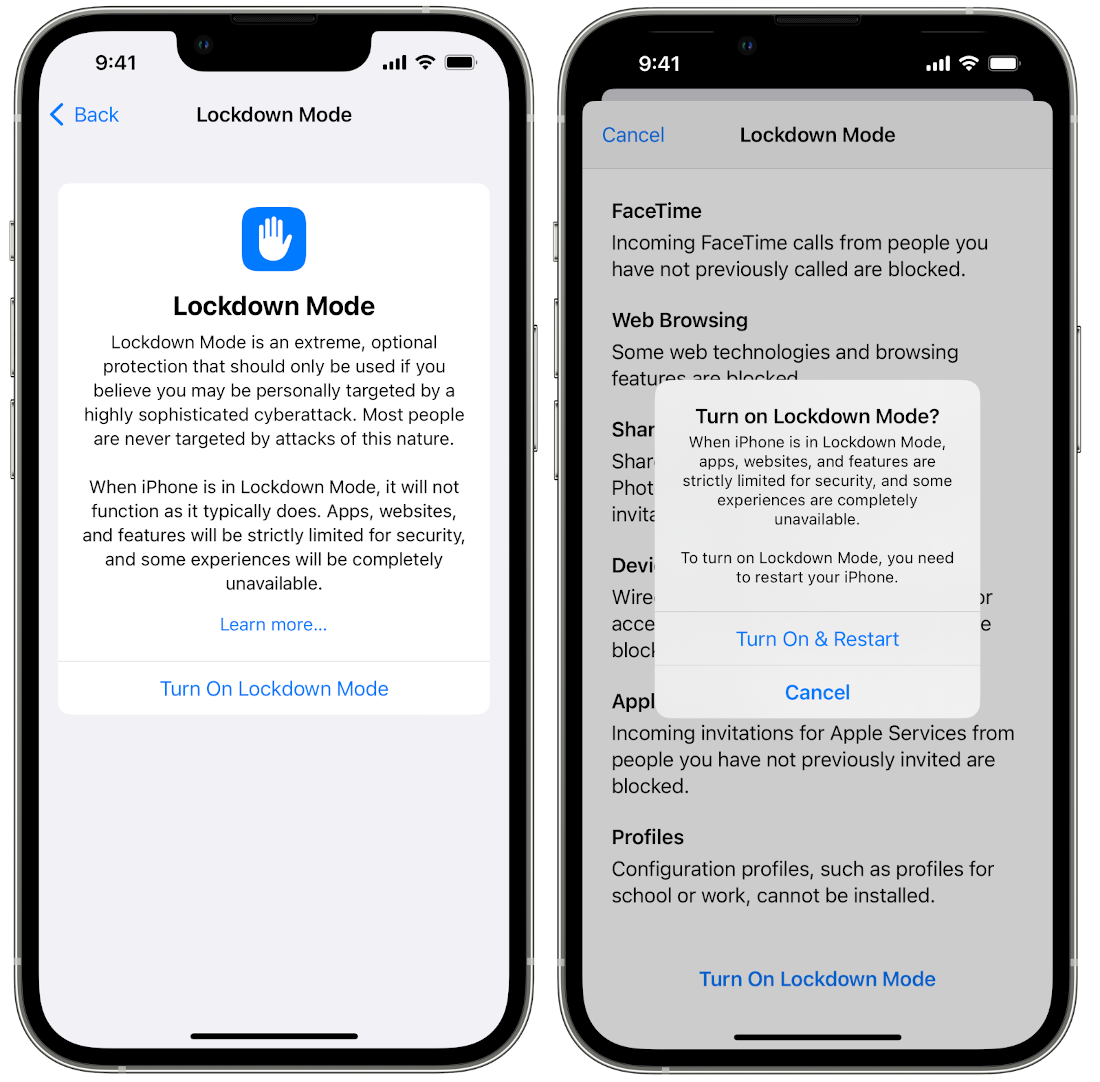
It’s also worth noting that people who believe they’re at risk of highly-targeted cyberattacks can use an extreme protection measure called Lockdown Mode. This is an optional feature that Apple introduced with iOS 16 macOS Ventura which greatly limits the attack surface for hackers, with the trade-off being that apps, websites, and OS-level features won’t work as expected.
Image credit: Ameen Almayuf, Maarten Dirkse
[ad_2]
Source link