[ad_1]
A hot potato: QNAP is once again warning users about a security vulnerability impacting its network-attached storage (NAS) devices. The critical flaw could make remote attacks easier, hence owners are strongly recommended to install the latest firmware updates.
Taiwanese company QNAP recently disclosed a new security vulnerability in the operating system of its NAS devices, a dangerous flaw classified with a “critical” severity level, which could spell doom for remotely-accessible user data. Patches are already available, while users should always install the latest updates to keep their NAS storage units safe from cyber-criminals and ransomware gangs.
According to QNAP’s official security bulletin, the flaw classified as CVE-2022-27596 affects QTS 5.0.1 and QuTS hero h5.0.1 NAS operating systems. If exploited, QNAP warns, the SQL injection vulnerability could allow remote attackers to inject malicious code. Potential attacks don’t require authentication, so QNAP assigned the bug a CVSS score of 9.8 out of 10.
The company has already fixed the vulnerability, releasing the following updates for its NAS operating systems:
- QTS 5.0.1.2234 build 20221201 and later
- QuTS hero h5.0.1.2248 build 20221215 and later
Users are urged to install the updates by going through QTS/QuTS control panel while logged as administrators, or by downloading the update directly from QNAP website’s download center. The Product Support Status page is also available to check for the latest updates available for every NAS model supported by the company.
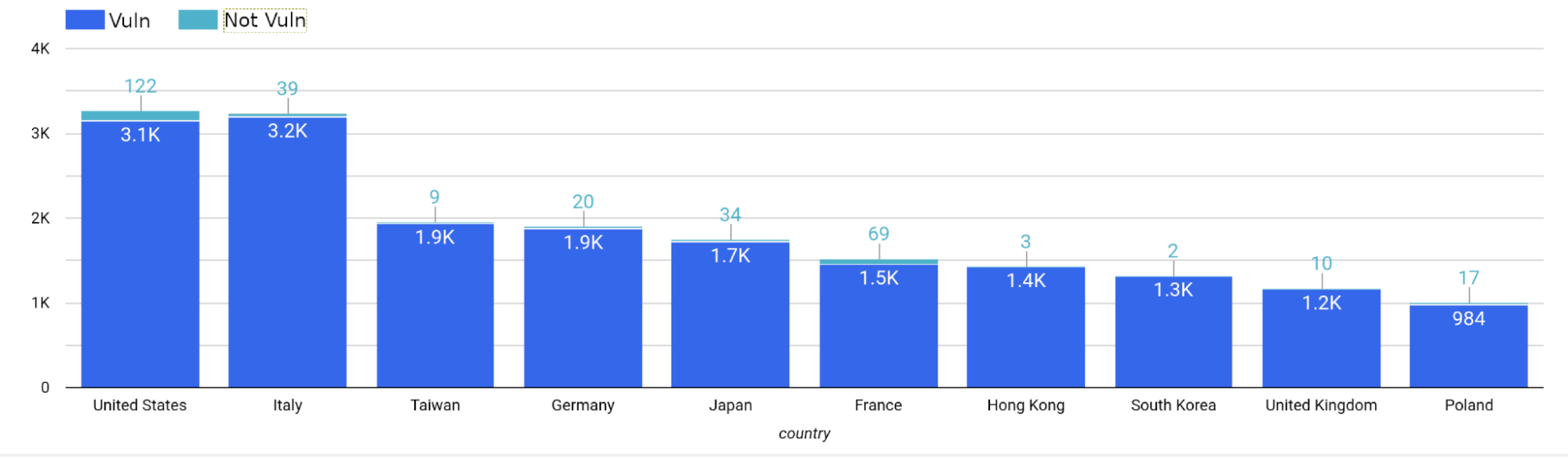
Security company Censys identified 67,415 online hosts running a QNAP-based system, while obtaining the OS version number for just 30,520 of them; over 98% of the identified QNAP devices were vulnerable to the CVE-2022-27596 flaw. Very few devices were patched, with only 557 running QuTS Hero h5.0.1.2248 or later and QTS 5.0.1.2234 or later.

Censys said that 29,968 hosts are still affected by the vulnerability, with many of them residing in the United States and Italy. There is no published exploit or proof-of-concept yet, but whenever the code is released in the open the data of thousands of QNAP users will be in extreme danger.
It’s “very likely” that CVE-2022-27596 could bring yet another successful ransomware campaign against user data stored on NAS devices reachable via internet. Censys said that the Deadbolt ransomware is already geared to target QNAP NAS devices specifically, so the cyber-criminals could use a future exploit or PoC to spread the same ransomware again.
[ad_2]
Source link