In brief: Don’t look now, but your video recorder might be part of a massive botnet pulling off record-breaking sustained DDoS attacks. The network involves compromised Shenzhen webcams and DVRs. The attacks do not appear state-sponsored, but they are very disruptive, with some victims reporting denial of service attacks lasting for days.
Nokia security researchers are tracking a botnet, dubbed Eleven11bot, that has been delivering what is likely the largest directed denial-of-service attack ever recorded. An estimated 30,000 webcams and video recorders make up the massive botnet. The network is international, but Nokia says the highest concentration of compromised devices (24.4%) is in the United States. While not the largest botnet ever recorded, it has pulled off the biggest observed attack ever seen, peaking at 6.5 terabits per second, surpassing the previous record of 5.6 Tbps set in January, according to Cloudflare.
Nokia’s Deepfield Emergency Response Team detected Eleven11bot after a surge of geographically dispersed IP addresses launched several “hyper-volumetric attacks” in late February. Unlike traditional exhaustive DDoS attacks that target server resources, volumetric attacks flood networks with massive amounts of data to overwhelm bandwidth capacity. Eleven11bot’s hyper-volumetric attacks have targeted communication service providers, game hosting infrastructure, and other sectors, causing disruptions that have lasted up too a week in some cases.

Nokia security researcher Jérôme Meyer noted that most IP addresses involved in these attacks had not previously been associated with DDoS activity, making Eleven11bot’s sudden emergence particularly concerning. He also pointed out that the last comparable botnet of this scale was observed in 2022, shortly after the Russian invasion of Ukraine, with approximately 60,000 infected devices.
“This botnet is much larger than what we’re used to seeing in DDoS attacks,” Meyer said. “Attack intensity has varied widely, ranging from a few hundred thousand to several hundred million packets per second (pps).”
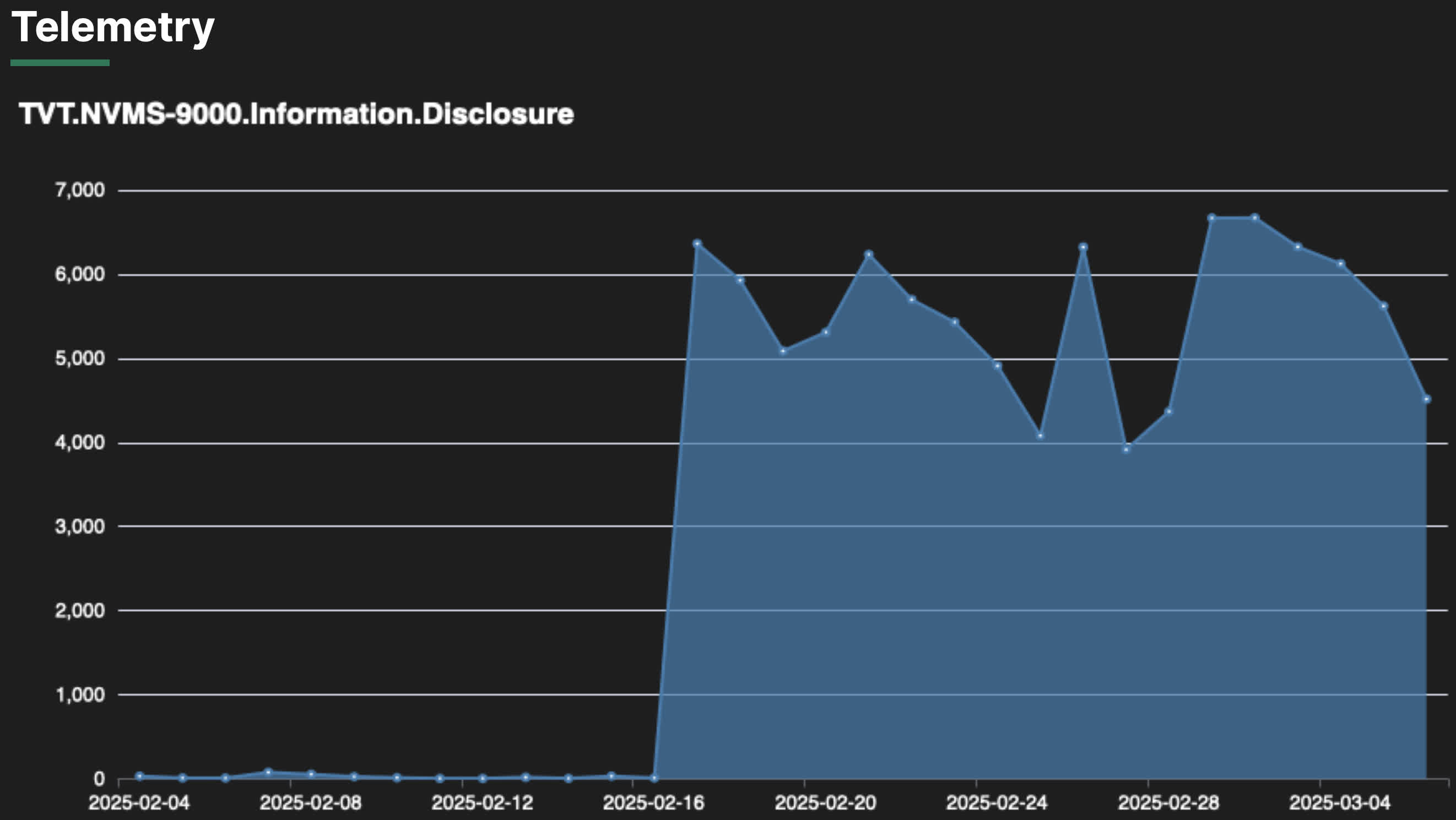
While Nokia initially estimated the botnet to consist of around 30,000 devices, the nonprofit Shadowserver Foundation revised this figure to more than 86,000. Conversely, security firm Greynoise countered with a much lower estimate of fewer than 5,000 devices, with the highest IP activity (61%) originating in Iran. Meyer said Shadowserver’s figure was probably an overestimate due to how it identified infected devices, mistakenly assuming that unique device information meant a device was compromised. He remains confident in his team’s estimate as repeated attacks originate from the same 20,000-30,000 observed IP addresses.
Greynoise researchers believe Eleven11bot is a new variant of Mirai, the infamous malware that first surfaced in 2016. Mirai-based botnets typically infect Internet of Things (IoT) devices by exploiting default credentials or software vulnerabilities. Researchers believe the Eleven11bot variant uses a newly discovered exploit to compromise Shenzhen TVT-NVMS 9000 digital video recorders running on HiSilicon chips.
To protect against Eleven11bot or any other botnet, experts recommend placing IoT devices behind firewalls, disabling remote administration when not needed, and ensuring devices have strong, unique passwords. Regular firmware updates are also critical in patching vulnerabilities that botnets like Eleven11bot could exploit.
Source link