[ad_1]
What just happened? A whistleblower has leaked files from a Moscow-based defense contractor that allegedly show how the company works with Russian military and intelligence agencies to support them in hacking operations, training operatives, spreading disinformation, and scanning the internet for vulnerabilities.
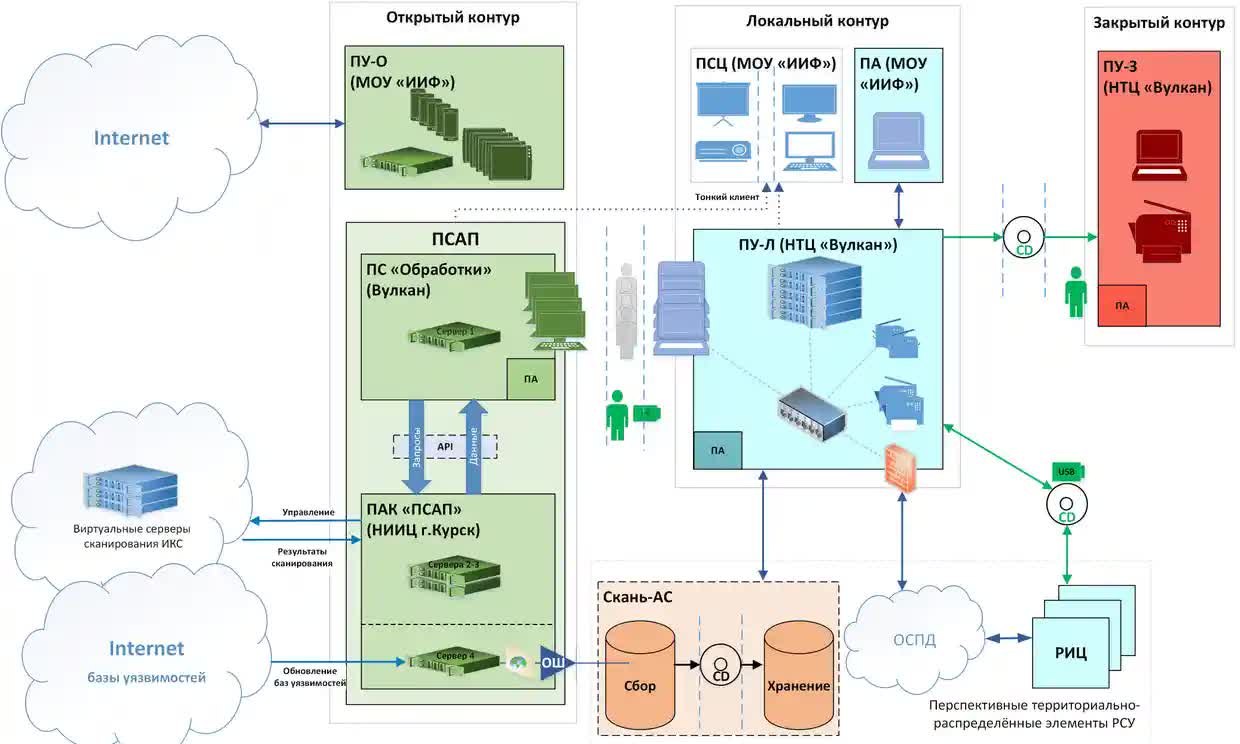
An anonymous whistleblower angry over the Ukraine war provided the documents on Moscow IT consulting agency NTC Vulkan. Journalists from several publications, including The Guardian, have been working with the source and just published tell-all articles, referred to as The Vulkan Files.
The files’ authenticity has been confirmed by five Western intelligence agencies and several independent cybersecurity companies. They link a Vulkan cyber-attack tool with hacking group Sandworm, which the US government said twice caused blackouts in Ukraine and disrupted the Olympics in South Korea. It is also thought to be behind the launch of NotPetya.
The tool, codenamed Scan-V, scans the internet for vulnerabilities, storing what it discovers for later analysis and for use in cyberattacks. Another, called Amezit, is described as a framework for controlling the online information environment and manipulating public opinion through methods such as creating fake social media profiles. It is also used to “enhance psychological operations, and store and organize data for upstream communication of efforts.”
Another system, Crystal-2V, is a training program for operatives that explains the methods required to coordinate attacks on rail, air, and sea infrastructure.
The source approached the German newspaper Süddeutsche Zeitung days after the Ukraine invasion last year. They said the GRU, the intelligence division of Russia’s armed forces, and the FSB, the country’s federal security service, “hide behind” Vulkan.
“People should know the dangers of this,” the whistleblower said. “Because of the events in Ukraine, I decided to make this information public. The company is doing bad things and the Russian government is cowardly and wrong. I am angry about the invasion of Ukraine and the terrible things that are happening there. I hope you can use this information to show what is happening behind closed doors.”
The cache of more than 5,000 pages of documents, dated between 2016 and 2021, also contains emails, internal documents, project plans, budgets, and contracts. Russia has repeatedly targeted Ukraine’s computer network, but there is no definite evidence of Vulkan-created tools being used in real-world attacks.
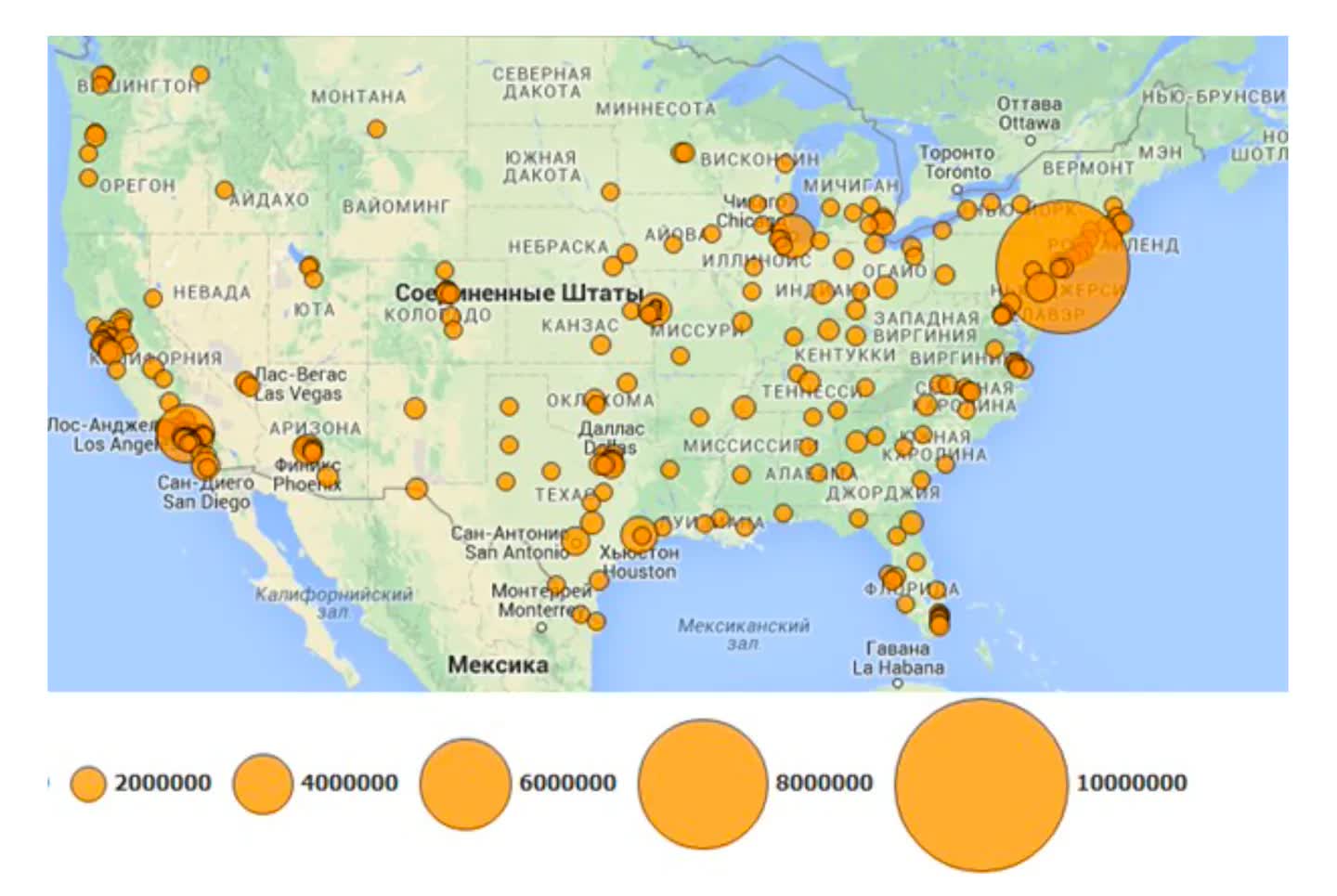
One of the most concerning parts of the leak is what appears to be illustrations showing potential targets. One is a map containing circles across the US that appear to represent clusters of internet servers; another shows details of a nuclear power plant in Switzerland. There’s also a document showing engineers recommending Russia add to its own capabilities by using hacking tools stolen in 2016 from the US National Security Agency and posted online.
The documents do not include verified targets, malicious software code, or evidence linking the company to known cyberattacks.
NTC Vulkan and Kremlin officials have refused requests for comment.
Earlier this month, Russian President Vladimir Putin and China leader Xi Jinping announced they intend to make their respective countries world leaders in IT, cybersecurity, and artificial intelligence. They released a document outlining their ambitions, which included a section stating, “Both sides support the United Nations Ad Hoc Committee to develop a comprehensive international convention against the use of information and communication technologies for criminal purposes.”
[ad_2]
Source link