The big picture: A breach at TeleMessage highlights a critical vulnerability in modifying end-to-end encrypted messaging apps to include archiving features. While TeleMessage claims it preserves Signal’s encryption during communication, the process of capturing and storing decrypted messages for archival purposes inherently introduces new security risks. Once these messages are archived on external servers, they become susceptible to unauthorized access if those systems are not properly secured.
An investigation by 404 Media has uncovered a major security breach at TeleMessage, an Israeli company that provides modified versions of encrypted messaging apps – most notably Signal – to US government agencies and private-sector clients for message archiving. The breach, which exposed sensitive communications, has raised urgent concerns about the security of high-level government and organizational messaging.
The issue gained public attention after a Reuters photograph captured Mike Waltz, a former National Security Adviser to Donald Trump, using a Signal-like app during a cabinet meeting. The app, TeleMessage, closely mimics Signal’s interface but is designed to retain and archive messages for compliance purposes – unlike the original Signal, which is built for privacy and strict end-to-end encryption.
Waltz’s use of TeleMessage drew further scrutiny after it was revealed that he had created a Signal group chat to share live updates on US military operations in Yemen. That group chat was accidentally shared with a journalist.

404 Media reports that a hacker exploited a vulnerability in TeleMessage’s backend system, gaining access to archived messages from some users. Alarmingly, the breach was relatively easy: the hacker claimed it took only 15 to 20 minutes to gain access, using credentials found in intercepted data to enter the backend panel, where they could view usernames, passwords, and message content.
The hacker told 404 Media they were motivated by curiosity about the app’s security and chose not to report the vulnerability to TeleMessage, fearing the company might attempt to cover it up.
While the hacker did not access messages from Waltz or other Trump cabinet members, the incident revealed a critical flaw: archived chat logs are no longer protected by end-to-end encryption once they leave the user’s device and are stored on TeleMessage’s servers. The breach exposed direct messages and group chats not only from TeleMessage’s Signal clone, but also from modified versions of WhatsApp, Telegram, and WeChat.
Communications involving US Customs and Border Protection, the cryptocurrency firm Coinbase, financial institutions such as Scotiabank, and the Intelligence Branch of the Washington D.C. Metropolitan Police were among the compromised data.
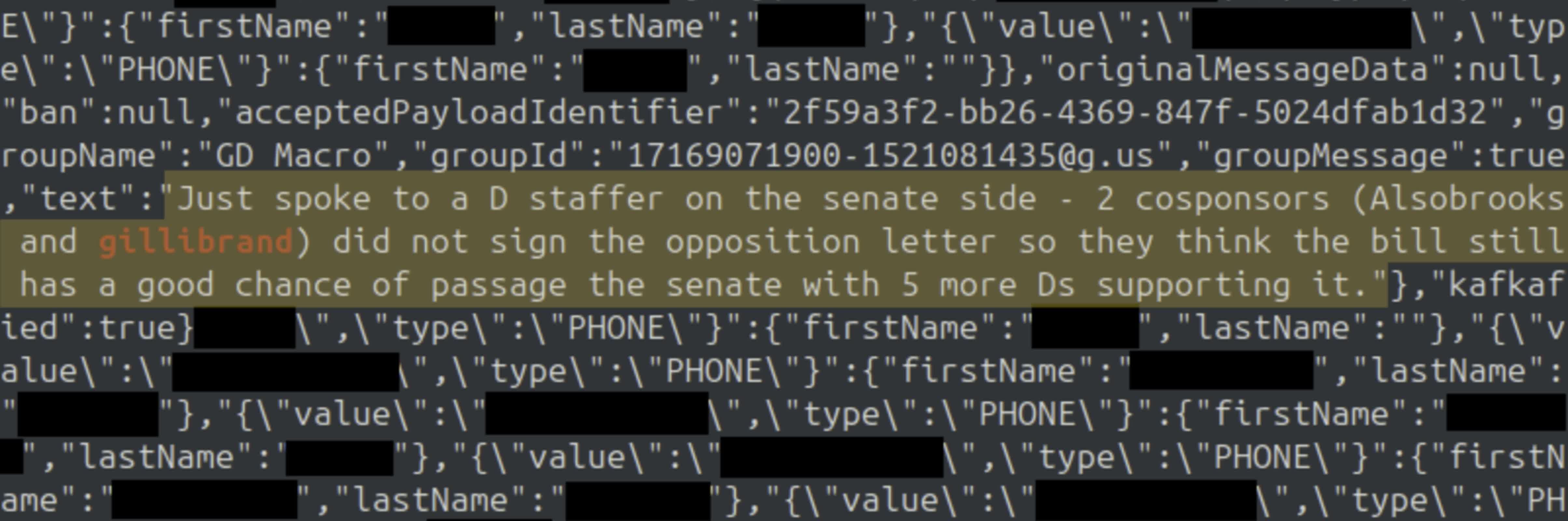
Screenshots and backend access shared with 404 Media also revealed a snippet of a conversation among Democratic lawmakers discussing their opposition to a cryptocurrency bill, highlighting the breadth of sensitive content potentially exposed.
The investigation further found that Waltz’s chats on the app included high-profile recipients who appear to be Marco Rubio, Tulsi Gabbard, and JD Vance, as evidenced in the Reuters photo.
The server hosting the archived messages was confirmed to be an Amazon Web Services endpoint located in Northern Virginia. This was verified by analyzing the modified Signal app’s source code and conducting HTTP requests to the server.
TeleMessage’s parent company, Smarsh, is currently rebranding the app as Capture Mobile. Tom Padgett, Smarsh’s president of enterprise business, told NBC News that the company’s role is to help clients comply with regulations by capturing and storing communications. Clients can choose from various archiving options, including storing messages in a Smarsh archive or forwarding them to a Gmail address.
However, Smarsh claims it is not the archive of record for any government agency. Padgett declined to specify which options federal clients use and would not confirm whether the Reuters photo showed Waltz using TeleMessage.
A Signal spokesperson emphasized that Signal has no agreement with TeleMessage, was unaware of the product before the Reuters photo surfaced, and cannot guarantee the privacy or security of unofficial versions of its app.
Public procurement records show that TeleMessage holds contracts with several US government agencies, including the State Department and the Centers for Disease Control and Prevention. These contracts span multiple administrations and are not limited to the Trump era. One active contract, awarded by the Department of Homeland Security and FEMA, allocates $2.1 million for mobile electronic message archiving and runs from February 2023 through August 2025.
Since the breach and subsequent media coverage, TeleMessage has removed much of its website content, including previously available service details and app download links.
Image credit: 404 Media
Source link
