What just happened? A significant vulnerability, known as EntrySign, has been uncovered by Google security researchers, affecting all AMD Zen processors from Zen 1 to Zen 4. This flaw allows attackers with local administrator privileges to bypass AMD’s cryptographic verification system and install custom microcode updates on affected CPUs.
The vulnerability stems from AMD’s use of AES-CMAC as a hash function in its signature verification process, which is a critical cryptographic error. AES-CMAC is designed as a message authentication code, not a secure hash function, making it unsuitable for this purpose.
The researchers discovered that AMD had been using a publicly available example key from NIST documentation since Zen 1, which allowed them to forge signatures and deploy arbitrary microcode modifications. These modifications can alter the CPU’s behavior at a fundamental level, enabling sophisticated attacks that persist until the next system reboot. For instance, the researchers demonstrated modifying the RDRAND instruction to consistently return predetermined values, effectively compromising the CPU’s random number generation.
To facilitate further research, Google’s security team has released zentool, an open-source jailbreak toolkit that allows researchers to create, sign, and deploy custom microcode patches on vulnerable processors. It includes capabilities for microcode disassembly, patch authoring with limited assembly support, and cryptographic signing functions.
The toolkit provides researchers with a platform to explore custom microcode updates and develop security features similar to those available for Intel processors.
AMD has responded by issuing microcode updates that replace the compromised validation routine with a custom secure hash function. These patches leverage the AMD Secure Processor to update the validation routine before x86 cores can process potentially tampered microcode. Although the attack requires local administrator access and does not persist through power cycles, it poses significant risks to confidential computing environments using technologies like SEV-SNP and DRTM.
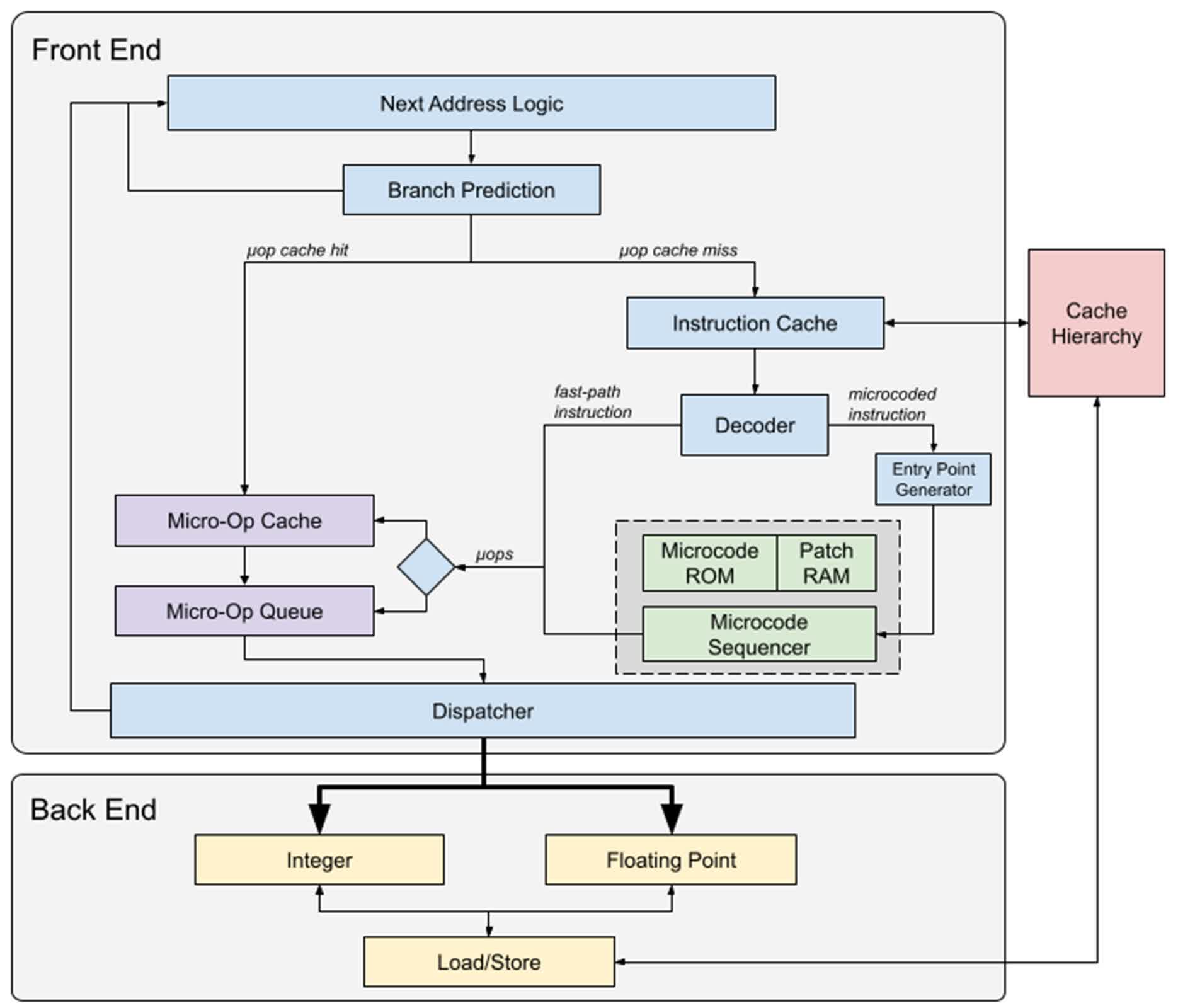
Modern x86 CPUs, including those from AMD and Intel, use microcode to implement complex instructions. These updates are crucial for patching hardware bugs without requiring costly hardware redesigns.
In the case of AMD Zen processors, microcode updates are double-checked against a series of strings and keys signed by AMD and confirmed against a hard-coded public key in the CPU. The EntrySign exploit works because AMD used AES-CMAC to allow researchers to reverse-engineer the security keys, preventing end-users from pushing unsigned microcode updates. Reusing a publicly accessible NIST example key as the security key further facilitated this exploit.
Source link