[ad_1]
In brief: Hacking commercial aircraft to cause complete navigation failures sounds like something you’d only see in movies, but an unknown group has been carrying out spoofing attacks on flights over the Middle East for weeks now. In one incident, a business jet almost strayed into Iranian airspace without clearance.
In September, OPSGROUP, an 8,000-strong international group of pilots, dispatchers, schedulers, controllers, and flight technicians, began highlighting incidents in which commercial aircraft in the Middle Eastern region received spoofed GPS navigation signals. These attacks also impacted the fallback navigation systems, resulting in total failure, writes Motherboard.
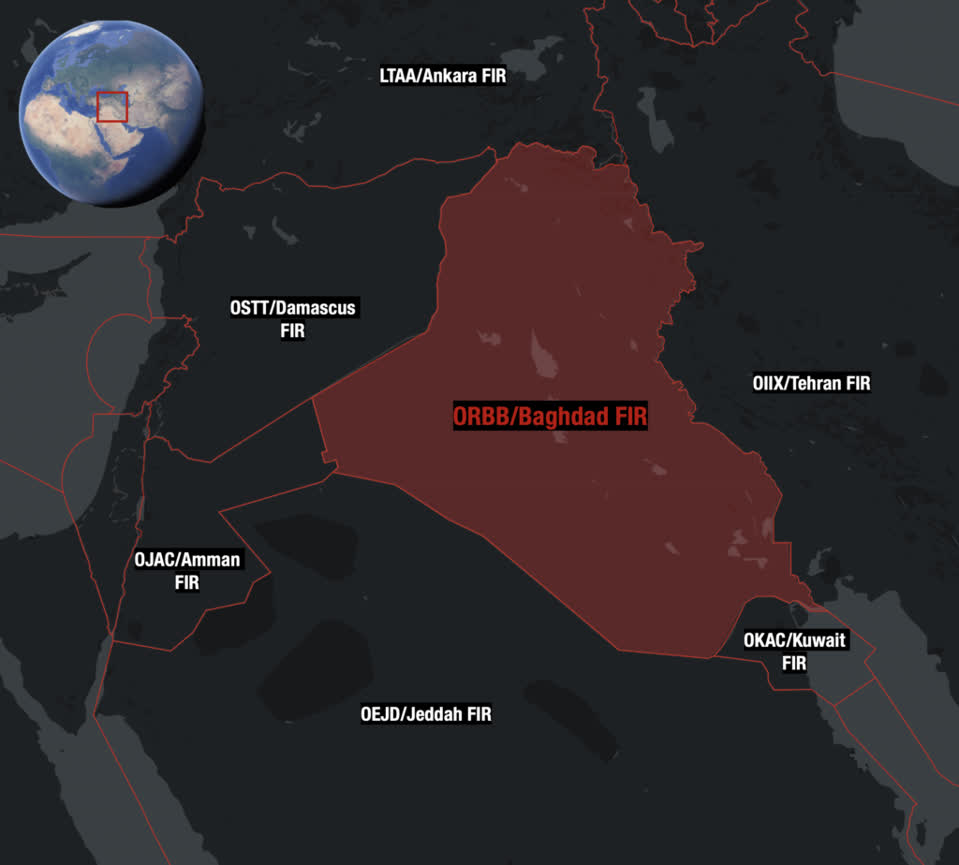
There have been more than 50 incidents in the last five weeks, centered around Baghdad, Cairo, and Tel Aviv. The attacks use a specific vector that OPSGROUP describes as “unthinkable” and exposes a “fundamental flaw in avionics design.” The spoofing affects the aircraft’s Inertial Reference System (IRS), used to help planes navigate.
“The IRS should be a standalone system, unable to be spoofed,” wrote OPSGROUP. “The idea that we could lose all on-board nav capability, and have to ask [air traffic control] for our position and request a heading, makes little sense at first glance – especially for state of the art aircraft with the latest avionics. However, multiple reports confirm that this has happened.”
One report says that an Embraer 650 business jet crew en route from Europe to Dubai lost both GPS navigation units aboard the airplane and GPS signals to both pilot/co-pilot iPads. The crew said the IRS didn’t work anymore, and they only realized something was wrong when the autopilot started turning left and right. After the aircraft flight management system showed a GPS error message, the crew requested radar vectors from air traffic control showing they were 80 nautical miles off course and had nearly entered Iranian airspace with no clearance.
UT Austin professor Todd Humphreys, who researches satellite communications, told Motherboard his team of students are constantly studying the signals in the region.
“Apart from run-of-the-mill jamming (e.g., with chirp jammers), we have captured GPS spoofing signals in our radio trawling,” he said. “But, interestingly, the spoofing signals never seemed to be complete. They were either missing key internal data or were not mutually consistent, and so would not have fooled a GPS receiver. They seemed to be aimed at denial of service rather than actual deception. My students and I came to realize that spoofing is the new jamming. In other words, it is being used for denial of service because it’s more effective for that purpose than blunt jamming.”
Humphreys said the new attacks were highly significant as unlike GPS jamming, spoofing, which he says acts like a zero-day exploit against aviation systems, also corrupts the IRS and backups, posing more of a threat to an aircraft’s safety.
GPS spoofing has also been used by Israel to try and protect itself from Hezbollah missile strikes, potentially endangering commercial aircraft. Israel has warned pilots landing in the country that they shouldn’t rely on GPS to land, instead relying on other methods.
[ad_2]
Source link