We’ve all been there. You try to log into your bank account with your username and password only to be met with a generic “incorrect password” error. You double-check your password manager, try a few variations, but after too many failed attempts, the system locks you out. Now you’re funneled into a tedious re-authentication process involving security questions you barely remember and a password reset form that smugly informs you, “New password can’t be the same as the old one.” You proceed to throw your device in frustration.
What is a Passkey?
A passkey is a secure, easy-to-use replacement for passwords. It uses your device’s built-in security (like Face ID, fingerprint, or a PIN) to log you into a website or service, without requiring you to remember or type anything.
The passkey is then stored on a secure element of your phone or computer, which means the website or service you’re accessing won’t need to store any passwords on their servers – reducing the risk of breaches or hacks.
In practical terms, you could say passkeys merge the concept of a password and 2FA (two-factor authentication) into one smooth action, but way more secure and way less annoying.
As an optional and recommended step, you can store your passkeys inside a secure password manager such as Proton Pass, 1Password, Dashlane, or Bitwarden. This allows you to sync and access your passkeys across multiple devices.
Creating a Passkey
Creating a passkey is easy, and the process is similar across most platforms. To illustrate, here’s how we set up a passkey for Amazon.com and used a password manager to store it…
First, I log into my Amazon account and navigate to the Login & Security section to access the passkey option.
Next, I click on “Add a passkey,” which creates a passkey specifically for Amazon. As shown in the screenshot, I had previously created a passkey that’s stored in my iCloud Keychain. You can create multiple passkeys for the same website and store them in different places.
Because I use Proton Pass and I have their browser extension installed, adding a passkey automatically opens Proton Pass to generate and store it. If I didn’t have Proton Pass installed, my web browser (Chrome, Firefox, etc.) would have stored the passkey instead.
Proton Pass will now save this specific passkey for Amazon, synced to my username. Since this is for Amazon, it also works for Amazon Web Services (AWS) accounts.
Why are Passkeys Needed?
According to NordPass’s research, the most popular password remains “123456” as of 2023 and 2024. The second most popular? “123456789.” Other common passwords are usually strings of sequential numbers or variations on “qwerty.” After six years of the same study, NordPass concludes that most people’s password habits haven’t meaningfully changed.
| Feature | Password + 2FA | Passkey |
|---|---|---|
| Steps | Multiple | Single |
| User needs to… | Type & wait | Just confirm |
| Security | Good | Better (phishing-resistant) |
| Convenience | Medium | High |
Passkeys are more secure because they eliminate password-based vulnerabilities, replacing passwords with cryptographic keys that protect users from phishing attacks, credential theft, and data breaches. Passkeys are protected by a single biometric factor, like your fingerprint or face, and no passwords are sent over the internet or stored on external servers.
Where Can I Use Passkeys?
While not every service has implemented passkey authentication, most popular sites have. Some of the major ones that support it include Amazon, Google, Apple, Github, Adobe, Uber, Microsoft, Nintendo, PlayStation Network, eBay, and Dropbox, as well as many social networks.
Financial institutions (banks) lag behind big tech giants in adopting passkeys, however companies like PayPal, Revolut and Robinhood already support it. Dashlane offers a helpful, community-driven directory of websites that have implemented passkeys login functionality.
You can already create passkeys using Google, Microsoft, or Apple devices. Many password managers – such as Proton Pass, Dashlane, 1Password, Bitwarden, and LastPass – also support passkey creation. As mentioned earlier, using a password manager allows passkeys to sync across devices.
It’s also important to remember that passkeys are unique to each website. The passkey you use to sign into your Google account is not the same as the one used for Amazon. That said, a helpful pro tip is to create a passkey for your Google account and then use Google’s authentication to sign in to other services (if the option exists). That way you can just use your one Google passkey while being able to access multiple websites.
How Passkeys Work (Technical Explanation)
Passkeys (technically known as Web Authentication or WebAuthn) are a technology that allows credentials to be authenticated without being stored on servers. They are part of the FIDO2 project, which aims to permanently replace passwords as a method of authentication.
The core concept relies on public key infrastructure (PKI). Instead of storing a username and password, passkeys are generated on an authenticator controlled by the user.
This authenticator could be your smartphone (Face ID, fingerprint), your operating system (e.g., Windows Hello), your browser, or a physical security key such as a YubiKey or Google’s Titan Key.
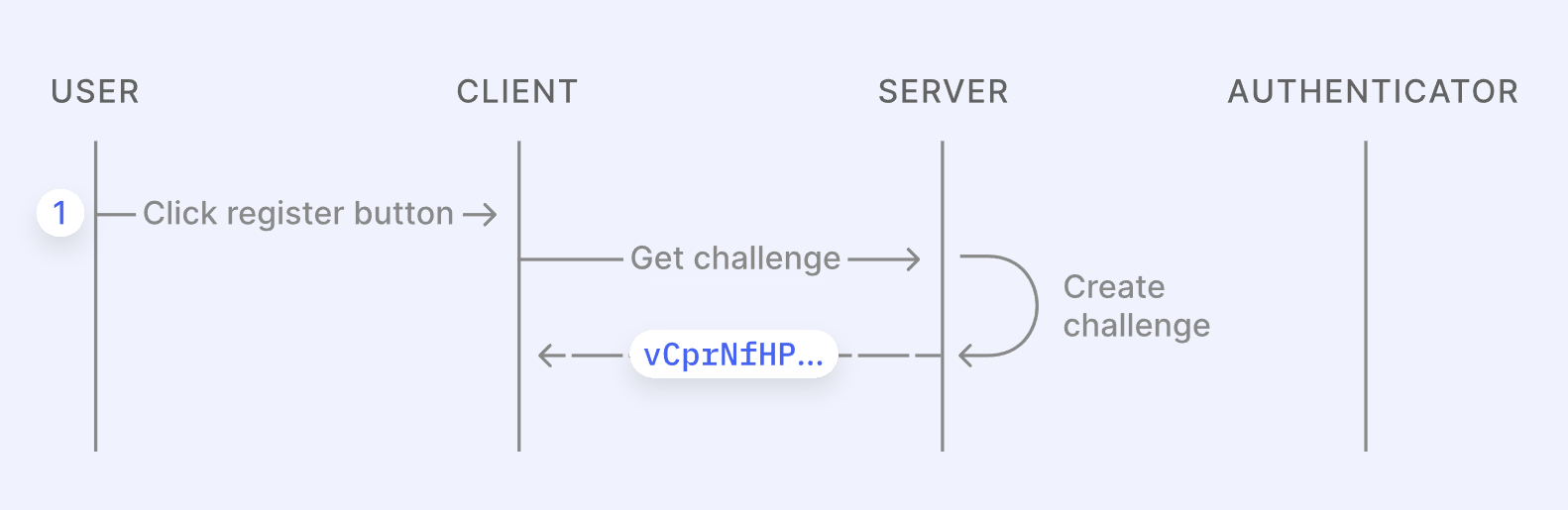
Creating a passkey is a 3-step process:
- The user clicks a button on a client (like Google) to create a passkey. This sends a request to the server, which responds with a randomly generated challenge string.
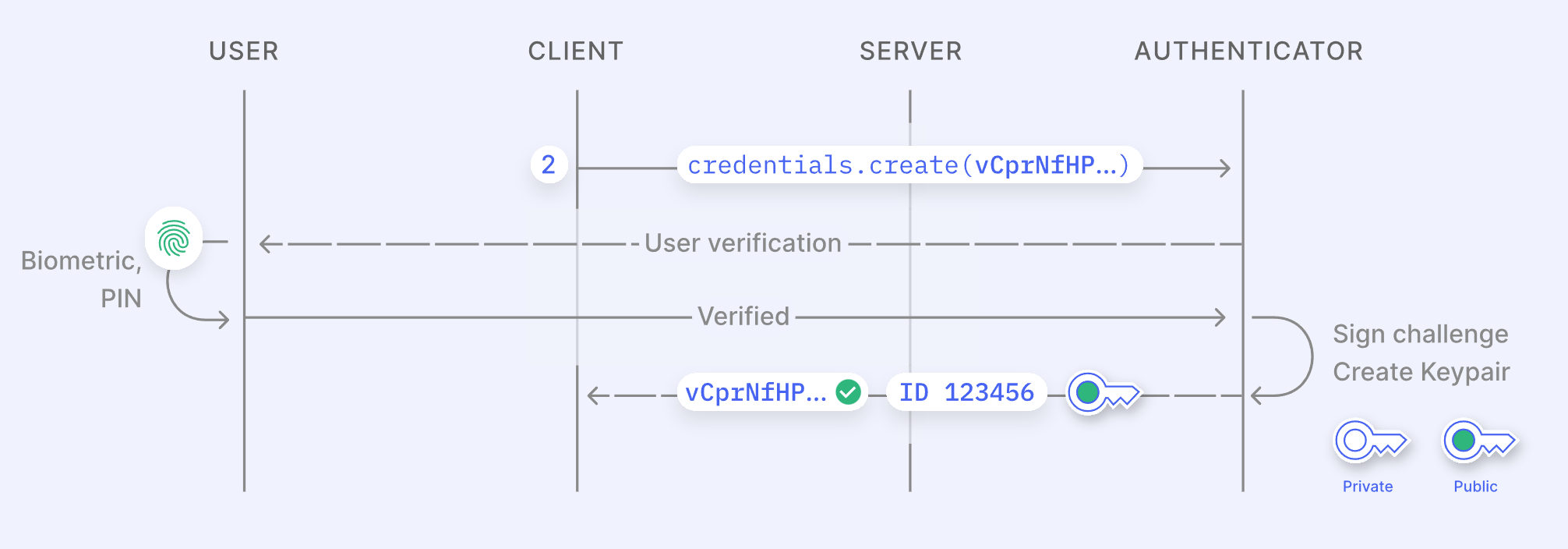
- The client calls the WebAuthn API along with the server’s challenge to create a private/public key pair. This key pair is generated and stored securely on the device in a secure element such as a Trusted Platform Module (TPM) chip or Apple’s iCloud Keychain. Depending on the client, the user is prompted for a PIN or biometric authentication (e.g., Face ID, Windows Hello, or fingerprint).
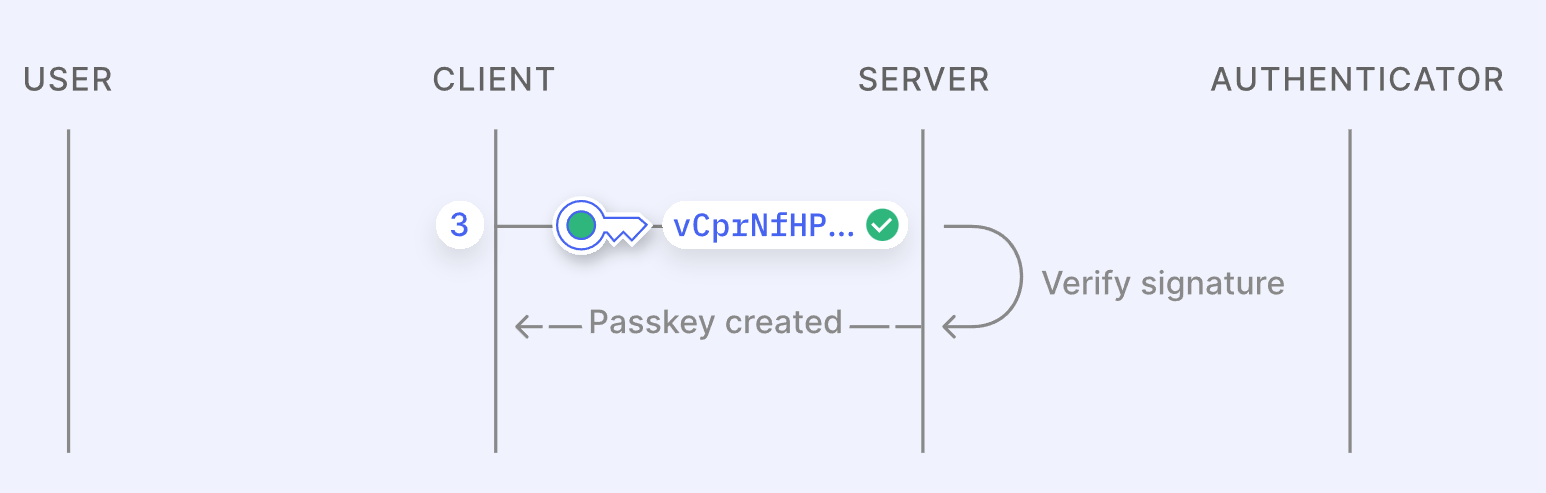
- The client sends the public key, credential ID, and the signed challenge (using the private key) back to the server. For future logins, the user authenticates via their device, which signs a new challenge and sends it to the server. The server validates this by matching the credential ID and public key to the signed challenge. If it checks out, the user is successfully logged in.
Frequently Asked Questions
What happens if I lose my device?
Passkeys require biometric authentication on your phone. Even if your phone is stolen, the passkeys can’t be accessed without your biometric data.
Can I share a passkey with someone else?
The purpose of passkeys is to provide personal, identity-bound authentication – not shared credentials. But technically, yes, there are ways to share passkeys.
For example, Apple allows passkeys to be shared via AirDrop under certain conditions. You can also share passkeys by logging into the same password manager.
Can passkeys prevent phishing attempts?
Absolutely. Phishing typically aims to steal usernames, passwords, or sensitive data. Passkeys don’t transmit credentials, making them useless to an attacker even if intercepted.
What if someone hacks the server or database?
At most, an attacker might gain access to the public keys stored in the database. Since these can’t be used to reverse-engineer your private key, your account remains secure. If needed, you can simply revoke the old passkey and generate a new one.
What about just using a password manager?
While password managers are a good step up from remembering passwords, they still rely on storing credentials on a server. Even open-source options like KeePass require a database of passwords. In contrast, passkeys provide a more secure and simplified solution by removing the need to manage or store multiple credentials.
Are there any scenarios where passkeys aren’t needed?
Yes. While passkeys offer a more secure and user-friendly alternative to traditional passwords, they aren’t necessary – or even ideal – in every scenario. Here are a few examples:
- Low-security accounts
If an account doesn’t store sensitive info (e.g., a throwaway forum account or a local news site), a strong password may still be “good enough.” -
Shared accounts
Passkeys are tied to you and your device. So for accounts shared among multiple people (like a shared Netflix account or business login), traditional passwords still work more flexibly – for now. -
Enterprise or legacy systems
Older corporate systems, VPNs, or internal tools may not support passkeys at all – some industries move slowly when it comes to adopting new authentication tech. -
Non-person entities (NPEs)
Developers using automated systems or scripts, they may need to authenticate to a server to perform tasks like scanning or data processing. In such cases, passkeys aren’t practical. This could also extend to software needing to use authentication for secure API calls.
Additionally, there are environments where passkey adoption just doesn’t fit yet. If you’re on a device that lacks cloud backup or passkey syncing, such as an older smartphone or a public computer, it can be difficult or impossible to use passkeys effectively.
So while passkeys are the future of authentication, there are still valid reasons to stick with passwords in certain contexts – for now.
Source link




