[ad_1]
In brief: There are an estimated 1.5 billion Apple devices in use as of 2021, all of which offer a convenient way to transfer files and images between them when they’re within Wi-Fi range. It’s been revealed that all those users are at risk of involuntarily sharing personal information with a malicious actor whenever they open a sharing pane.
If you happen to own more than one Apple device — say, an iPhone and a Mac — chances are you’re already familiar with AirDrop. There’s something to be said about the convenience of transferring documents, images, and more from devices nearby. No need to use thumb drives or to email things to yourself or to family and friends, especially if those devices are connected to the same Wi-Fi network or if they’re within 30 feet of each other.
There’s only one small problem — AirDrop has a flaw that allows anyone within Wi-Fi range to see your email address and phone number as soon as you open the sharing pane on your iOS or macOS device. This was discovered by researchers at the Technische Universitat Darmstadt, who notified Apple about the vulnerability in May 2019.
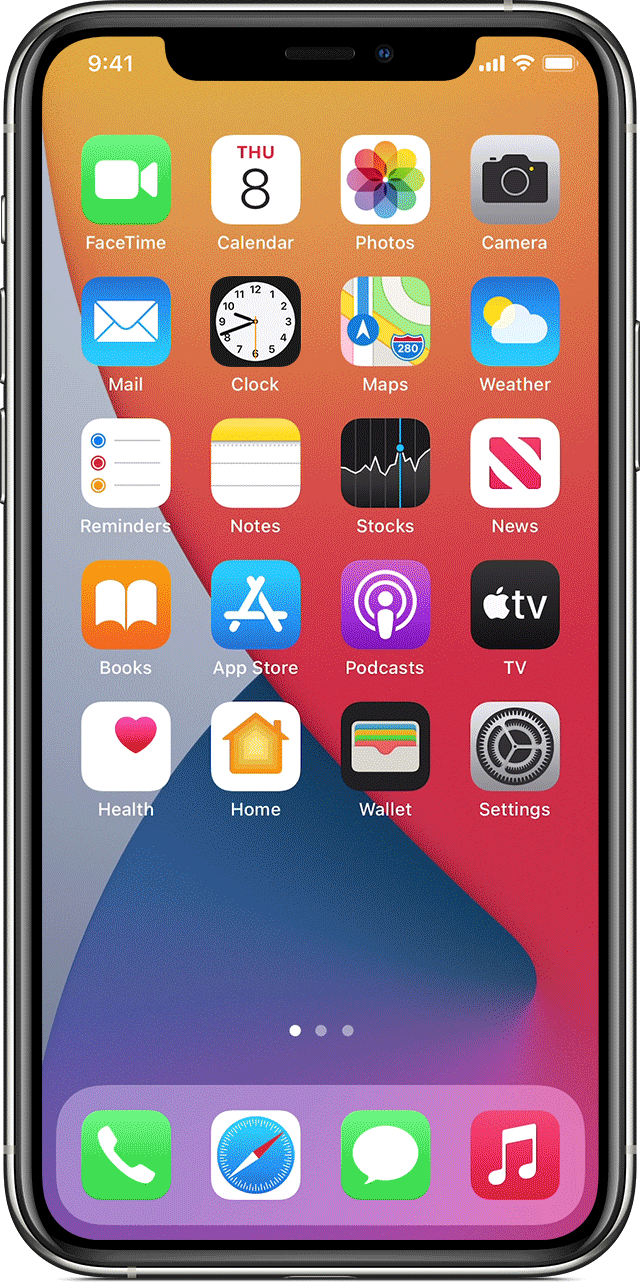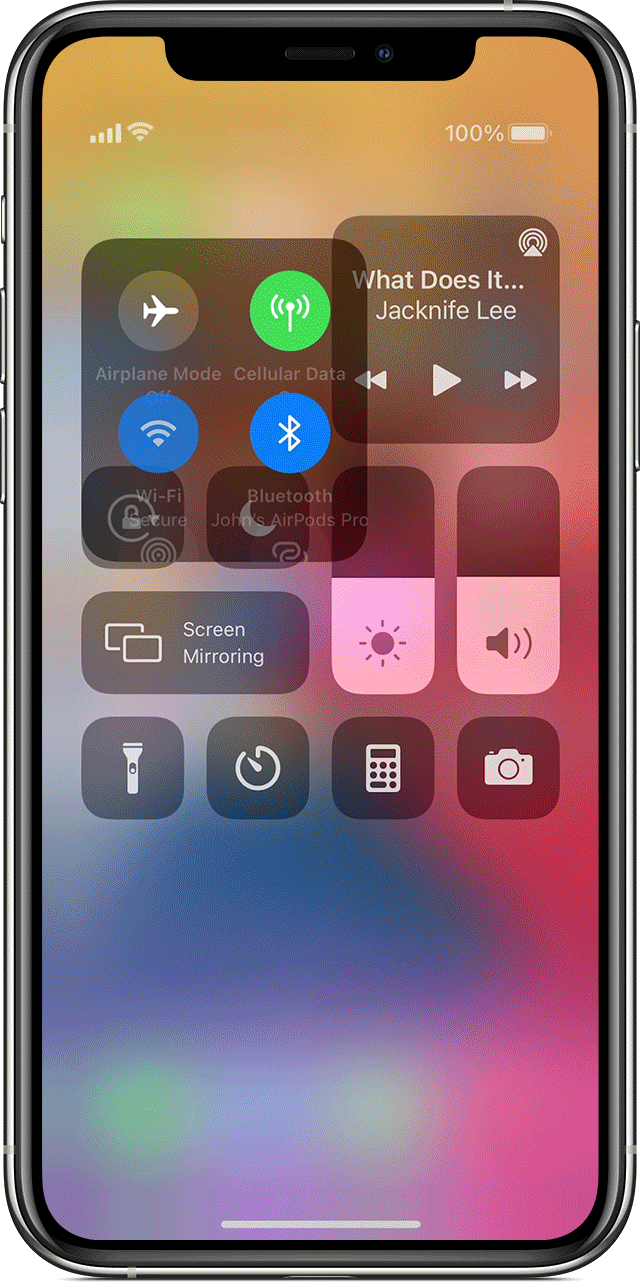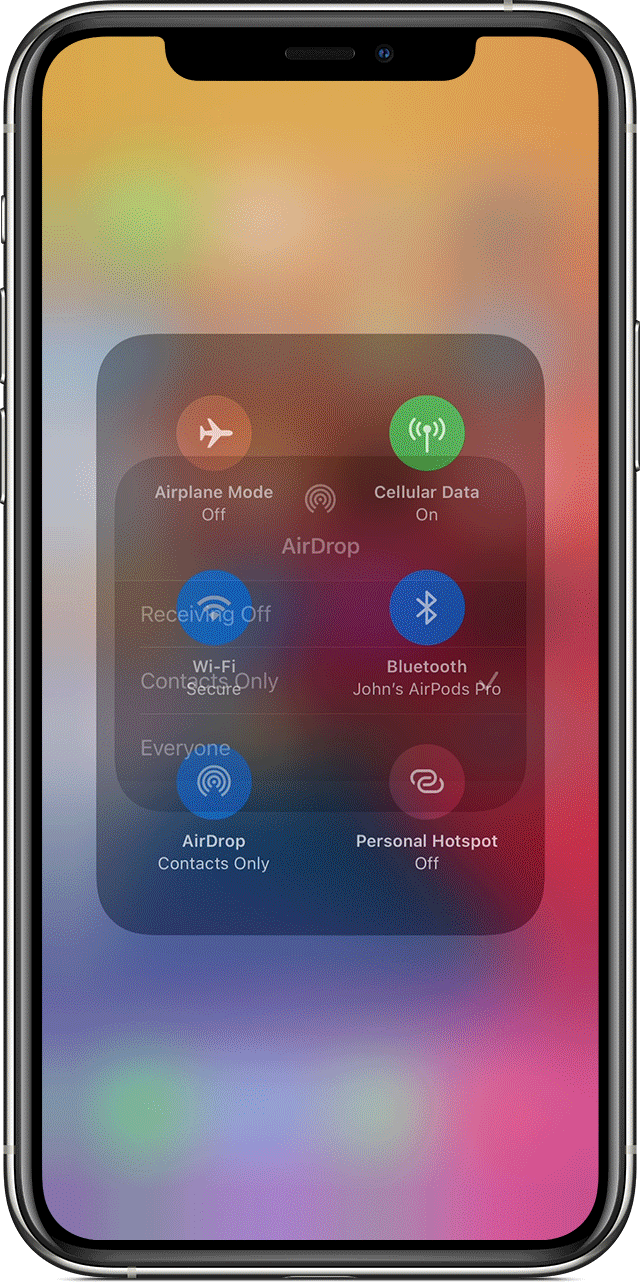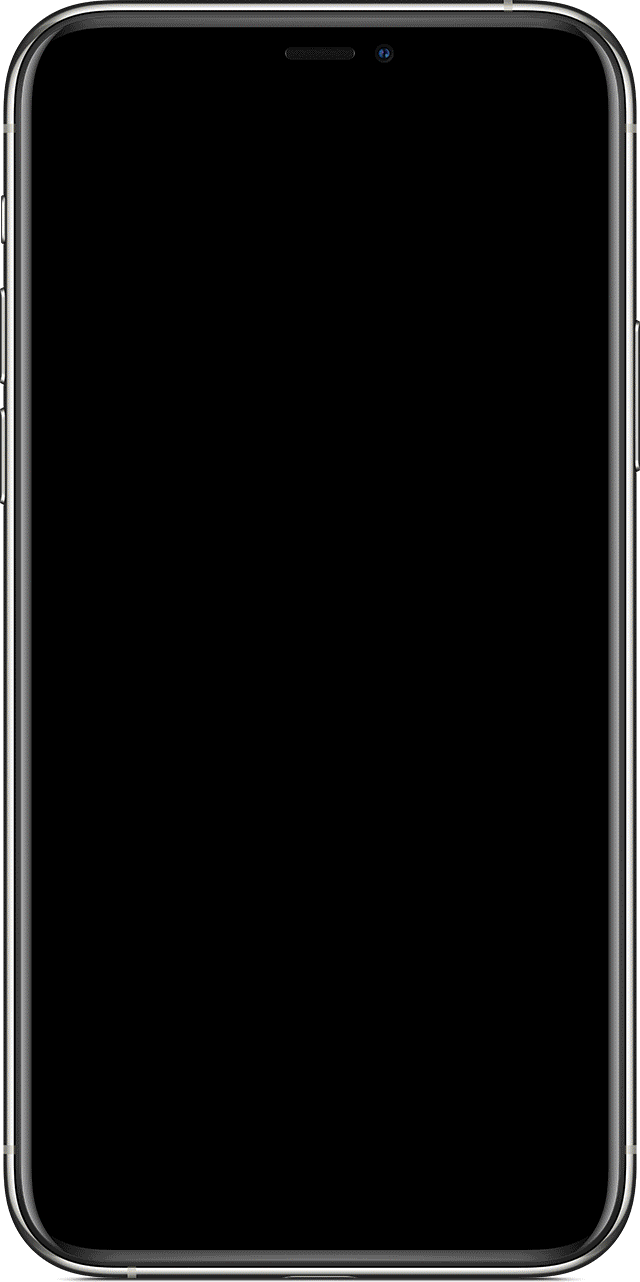
Since then, Apple has done nothing to fix the issue, despite the fact that it affects 1.5 billion devices currently in use around the world. The default setting for AirDrop on all of these is “Contacts Only,” with the possibility to change that to “Everyone” or “Receiving Off.”
By default, AirDrop’s mutual authentication system checks if the sending and receiving device are either both owned by the same person or that they’re owned by people who are in each other’s Contacts list. During that process, the sensitive data being exchanged between devices is encrypted, but researchers note the resulting identity hashes are weak enough to be broken using brute-force attacks.
At this point, it’s not clear why Apple hasn’t fixed the issue, especially since the security researchers also offered a proposed solution they dubbed PrivateDrop which makes the contact discovery process more secure while having a minimal impact on the authentication delay. Otherwise, the only way to mitigate the vulnerability is to disable AirDrop discovery altogether, but that would make the feature a lot less convenient.
[ad_2]
Source link