[ad_1]
In brief: Researchers from security firm Human Security recently disclosed one of the largest and most sophisticated mobile advertising attacks they’ve seen to date. Dubbed Vastflux, the well-orchestrated campaign impacted millions of phones and defrauded hundreds of ad companies and app makers – and likely made its operators boatloads of cash.
Vastflux was first detected by Human Security last year while working on a separate threat. It worked by targeting a single advertising slot rather than a user’s entire phone or an entire app. Once the group won an ad slot via advertiser auction, they would insert malicious code allowing them to stack multiple video ads on top of each other.
The end user would only see a single video ad but behind the scenes, the attacker was actually feeding them up to 25 video ads stacked on top of each other. They would get paid for each ad as if they were shown individually, and the group spoofed details from hundreds of apps to make it appear as if multiple apps were involved in the campaign. Furthermore, the attack only allowed certain tags to be attached to help stay under the radar. Multiple domains were also used to launch attacks.
From the end-user standpoint, the only hint that something was amiss was faster battery drain as your phone processed all the fraudulent ads in the background.
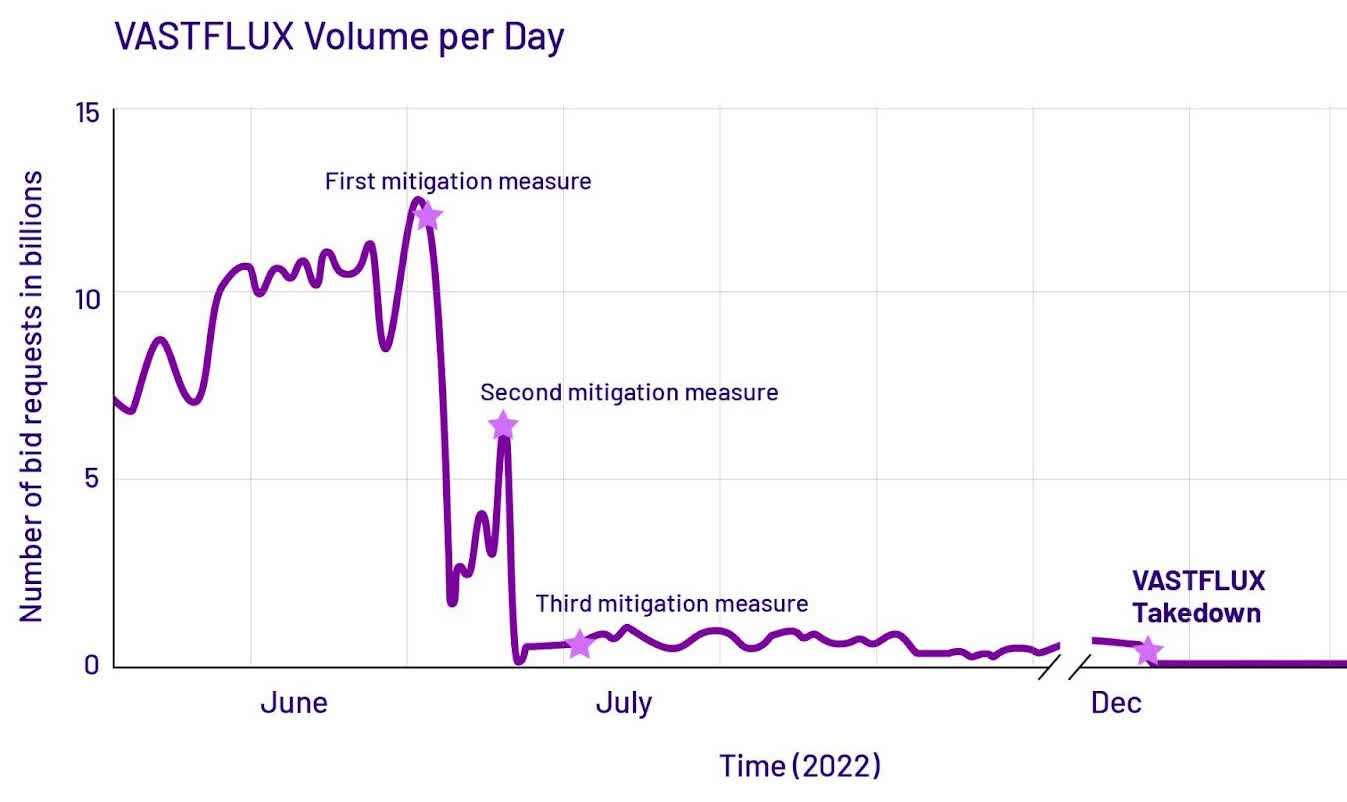
Human Security has not yet named the group behind the attack nor have they said how much they potentially made off the scheme, but it is likely a hefty sum. At its peak in June 2022, the attack was making 12 billion ad requests daily. Vastflux primarily targeted iOS devices but some Android handsets were also hit. In total, it is believed that around 11 million devices were impacted.
Last summer, the security firm and its partners went on the offensive with a series of mitigation measures. By December, the group behind the campaign took its servers offline and has been radio silent since.
Image credit: Tima Miroshnichenko
[ad_2]
Source link